CRA Products and their components
The European Union (EU) Council has adopted the Cyber Resilience Act, following the final text being adopted by the EU Parliament in September. This legislation came into effect in December 2024. The CRA aims to create a baseline cybersecurity standard for products with digital elements placed on the EU single market. This will reduce security vulnerabilities in products being made available in the EU and consequently reduce the number of cybersecurity incidents that leads to data loss and theft, cybercrime such as ransomware attacks or cyberespionage.
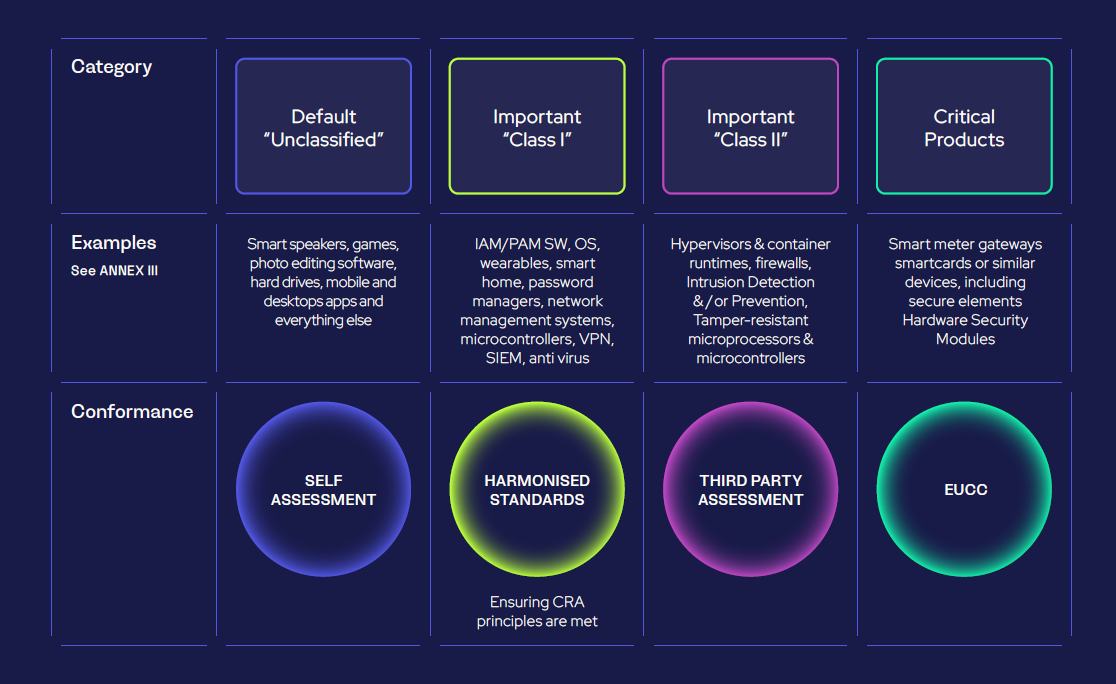
The products that are in scope for the CRA will fall into different categories based on their risk level and criticality. Depending on the category the conformance requirements will be different. Most products will fall into the default category which is low risk. In this article we will explain the different categories, given some examples of products in each category and explain what kind of an assessment will be required before placing the product on the market.
Default (Lowest Risk Category)
Approximately 90% of products fall into this category, which has a lower risk profile compared to other categories. Examples include:
- Smart home devices
- Printers
- Bluetooth speakers
- Media player software applications
Manufacturers with products in the Default category can use self-assessment to demonstrate compliance with CRA essential requirements (as outlined in Annex I of the CRA) and follow the self-assessment protocol detailed in CRA Annex VIII.
Important Class I
The complete list of products that fall into Important Class I can be found in Annex III of the CRA, this includes;
- Identity management systems, privileged access management software & hardware, and access control readers
- Standalone & embedded browsers
- Password managers
- Software that searches for, removes or quarantines malicious software
- Products with virtual private network function
- Network management systems
- Boot managers
- Operating systems
- Routers and modems intended to connect to the internet and switches
Manufacturers with products that fall into Important Class I can use the self-assess method to demonstrate compliance with the CRA essential requirements as long as they can apply one of the following:
- Harmonised Standard – a European standard developed by a recognised European Standards Organisation, following a request from the European Commission. Manufacturers can use harmonised standards to demonstrate that products comply with an EU legislation. Harmonised standards are currently being created specifically for the CRA.
- Common Specification – a detailed practical set of rules setting out how a product should comply with specific requirements adopted by the European Commission when no harmonised standards exist.
- European Cybersecurity Certification – a scheme ENISA is developing on behalf of the European Commission to create a framework to certify products with digital elements meet the essential requirements of the CRA.
If the manufacturer cannot use one of these schemes for their product, they must apply to have their product assessed by a third-party conformity assessment body.
Important Class II
Product types that fall into Important Class II category include:
- Hypervisors and container runtime systems supporting virtualized execution of operating systems
- Firewalls, intrusion detection & prevention systems
- Tamper-resistant microprocessors & microcontrollers
Products in the Important Class II must complete a third-party conformity assessment even if they comply with harmonized standards, common specifications or a European cybersecurity certification scheme.
Critical Class
The Critical Class includes products of the highest risk and therefore have the strictest compliance process. These include:
- Hardware devices with security boxes
- Smart meter gateways
- Smart cards or similar devices including secure elements
- Other devices for advanced security purposes, including secure crypto processing
Products in the Critical Class must complete a European Common Criteria (EUCC) cybersecurity certification assessment conducted by a conformity assessment body.
Businesses should factor in the cost of compliance, as well as the additional time and effort required to bring new CRA compliant digital products to market successfully. Understanding which product category applies to their product is crucial, as this will determine the type of assessment they need to undergo, making it a key consideration when budgeting for future projects.
Components – who is responsible?
What if you have a product that contains components you obtained from a third-party that need to be compliant under the CRA? For example, you make a lamp that is voice activated, the lamp uses a microprocessor to interpret the voice command to turn it on or off. You bought the microprocessor from a third-party and therefore did not manufacturer it, but you will be using it as a component in a product you are manufacturing. Who here is responsible for making sure the microprocessor is compliant with the CRA?
Simply put it is the responsibility of the manufacturer of the microprocessor to make sure that it is compliant with the CRA if it is being sold in the EU. However, you as a manufacturer must ensure you do your homework on your third-party components. The CRA stipulates that manufacturers using third-party components must exercise due diligence to ensure they source components that do not compromise the security of their product. Manufacturers must report vulnerabilities they discover in a third-party component to the component’s manufacturer.
This gets a bit more complicated if you are sourcing a component from outside the EU. If the components manufacturer is selling directly into the EU then it is their responsibility to comply with the CRA. But if you are buying components and importing them from outside the EU, there is separate responsibilities for importers. You as an importer then become responsible for ensuring compliance with the CRA.
To find out more on the obligations for Importers and Distributors read our article here cyber-resilience-act-for-importers-and-distributors/
Obligations for Open-Source Components
Manufacturers using open-source components in their products must conduct due diligence by assessing the security of these components, checking for known vulnerabilities, and ensuring they receive regular security updates. They should document these components in the Software Bill of Materials (SBOM) and include integration details in the technical documentation. If vulnerabilities are identified, manufacturers must report them to the maintainers, remediate the issues, and share the fixes. They must implement coordinated vulnerability disclosure policies and ensure secure and prompt distribution of security updates. Compliance with cybersecurity requirements must be maintained, and for products qualifying as free and open-source software, technical documentation should be made public. Additionally, manufacturers must define and document the support period for their products, informing users about the presence of open-source components and providing instructions on handling security updates.



 Downloadable Assets
Downloadable Assets 
 Download File
Download File